Vehicle cybersecurity in a connected world
Cybersecurity is a process requiring vigilant monitoring.

Aug 10, 2021
Updated: Jan 2, 2025

We live in a connected world with everything from our bathroom scales and our home security systems to our vehicles regularly communicating with the internet and a host of other people and things. And while connecting vehicles to the internet provides many benefits, it, increasingly, is exposing the risk vehicles have to data theft and a host of other cybersecurity crimes as real possibilities.
What is the cybersecurity threat?
Today’s cars and trucks have seen an explosion in the number of electronic control units, and the lines of software code is expected to triple by 2030 to 300 million. This provides an abundance of complex software code and the increasing vehicle architecture and digitisation generates ample opportunity for cyberattacks.
The increasing prevalence and scope of cyberattacks and the looming threat they pose to fleets of vehicles is why Geotab has prioritised cybersecurity in all of its offerings.
The cybersecurity threat is no longer just a theoretical possibility – it’s now a hard reality.
Two recent examples in the United States, the Colonial Pipeline shutdown and the Solarwinds cyber attack show just how real cybercrime and cyberterrorism is. In the former, hackers were able to take over and shut down a major U.S. pipeline, creating shortages of fuel throughout the east coast and deep south. The Solarwinds cyber attack was even more insidious. Hackers attacked an IT firm and were able to spy on numerous U.S. companies and government agencies for months without detection.
Closer to home, UnitingCare Queensland was the victim of a cyber attack in April 2021 claimed by a notorious ransom gang, where it is suspected hospital patient data was threatened with destruction or publishing unless the victim paid a ransom.
And this threat is just as real for today’s internet-capable and connected vehicles.
What are the emerging cybersecurity threats?
There are three emerging ways that hackers or others could compromise a fleet operation that operates modern, connected vehicles, including:
- Data theft: Vehicles are generating tremendous amounts of valuable data, including detailed histories of activity related to a company’s operation as a whole. If this data was compromised by a hacker, it could have serious consequences, as a mid-sized trucking company in Texas recently found out the hard way when hackers stole customer data and held it for ransom.
- Vehicle takeover: The potential for a nefarious actor to gain control of a vehicle while a driver is behind the wheel has been demonstrated dramatically in a number of online videos and at hackathon conferences. While this threat is real, how and/or if this would occur in the way that has been demonstrated — a driver behind the wheel suddenly losing control of the brakes, radio, or mapping functions — is unknown. But as the Colonial Pipeline incident demonstrated, manipulating a physical piece of equipment is more than possible, and the consequences could be devastating.
- Sensor spoofing: In this scenario, thieves “trick” the vehicle’s sensors and/or cameras with the wrong information. This can take either the form of a device impersonating a control unit within the vehicle’s network broadcasting fraudulent sensor data or something external to the vehicle that interferes with a sensor producing false data or preventing data collection. A recent example of how this could affect a fleet occurred in South America in which a trucking company’s fleet was hacked and hidden from its tracking system, allowing thieves to steal physical cargo.
What makes the threat of vehicle-based cybercrimes even more insidious is that there is no single point of entry for hackers to gain access to a vehicle.
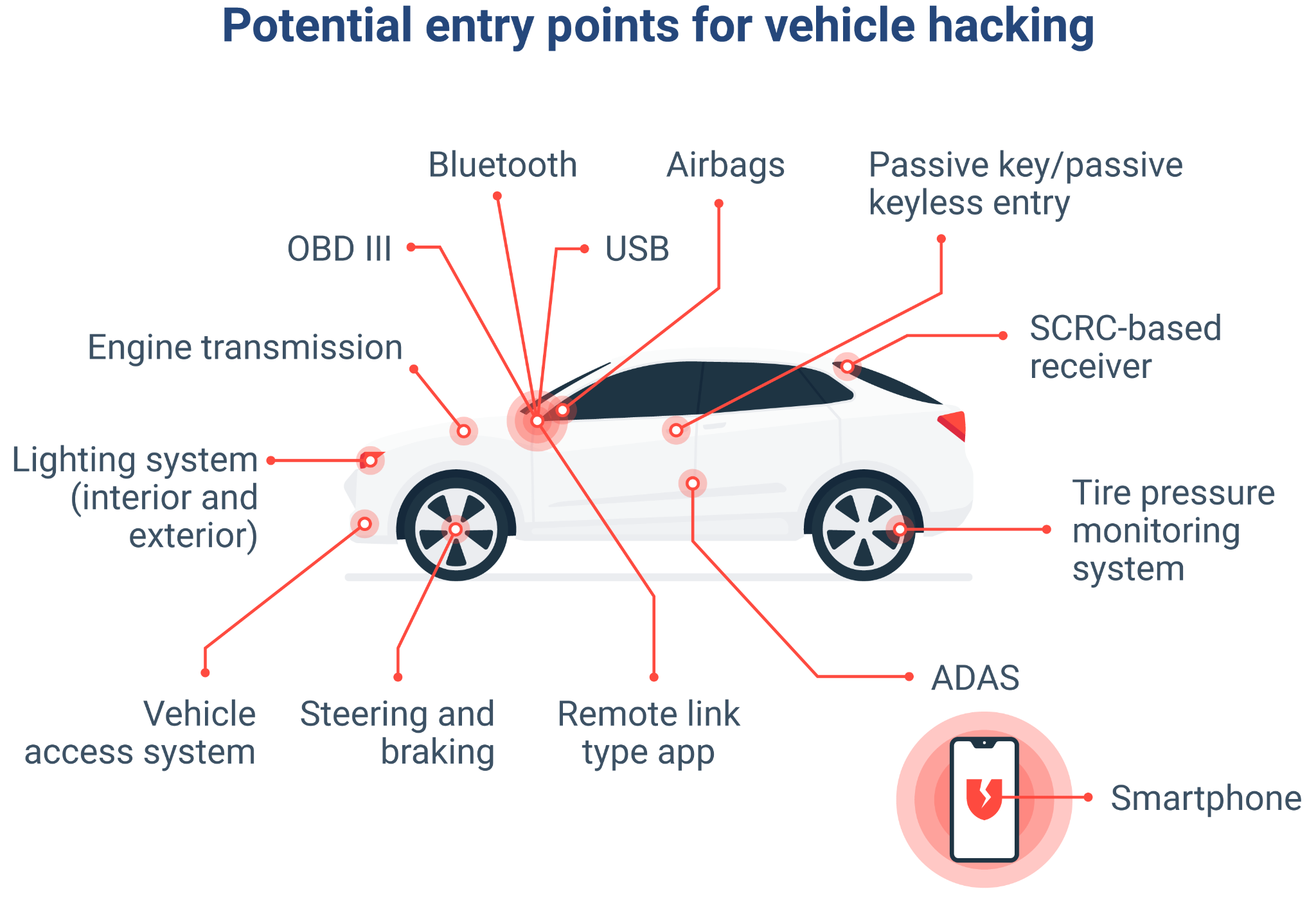
Overview of the potential entry points on a vehicle for cyber criminals
A quick internet search will reveal scores of successful, but so far benign hacks against many of the world’s major automotive brands using a number of these entry points. What these online examples are in fact is a proof of concept--hacking a vehicle is a real possibility.
How to increase the security of your fleet data
The hacking of a fleet, which could result in a fleet being shut down or compromised for a ransom, can be catastrophic. While manufacturers adopt international standards into their vehicle electrical architecture, a determined hacker will find a way to exploit gaps in security. Vehicle design is evolving, and was not previously a more mature security. That is why third-party oversight is critical to detect unusual behavior.
Therefore, whether you are a small business owner or a large fleet, it is critical to develop a unified and comprehensive cybersecurity plan across all makes and models of vehicles to prevent unauthorised third-party access.
The first steps to building your fleet cybersecurity plan is to understand:
- How your telematics data is handled and protected by your telematics provider.
- What security controls are in place by all companies, from vehicle manufactures to third-party aftermarket suppliers to ensure that your vehicle's critical operating systems are well protected.
Data security at Geotab
Geotab takes a meticulous approach to cyber and data security, and we continue to take extreme effort to secure the connection between the vehicle and the user interface. Our approach can be likened to physical door locks that keep the vehicle’s contents and the driver and passengers secure and private from outside threats. Our telematics security restricts access to the vehicle and driver’s data collected and stored in the devices, preventing unauthorised access to the end-to-end telematics solution.
Broadly, this is how Geotab keeps vehicle data secured. The Geotab GO device collects the data and encrypts it according to Federal Information Processing Standards (FIPS), a set of security standards developed by the U.S. government that are widely used by both government agencies and, voluntarily, by private organisations, becoming the becomes first telematics company to achieve FIPS 140-3 validation for its telematics device.
Once the data is sent to a secured, cloud-based solution, then it can be accessed through the use of logins using two factor authentication. Access is role-based, and must be assigned by a trusted administrator. Think of it as double or triple locking the door to your car — that’s the level of security you can expect on a day-to-day basis from Geotab’s solution.
From there, we go another step further. Geotab’s internal audit team is a dedicated and committed resource to monitor the risks and audit all the security controls to ensure the effectiveness of the controls. These additional security controls highlight the maturity of Geotab’s data security protocols and the importance we place on it.
Perhaps most importantly for the security of our clients including many US federal government client fleets, Geotab has become fully FedRAMP authorised, meeting the most stringent security requirements set forth by the U.S. Federal Government. This involves a daunting, multi-year process, and requires annual audits following certification. Because Geotab operates in over 130 countries, we see security in a global context and comply with all regional policies such as ISO 27001, and local privacy policies, such as CCPA and GDPR.
“Geotab’s unwavering commitment to rigorous organisational data security measures is reflected in the achievement of our FedRAMP ATO,” said Geotab CSO, Alan Cawse. “We are proud to provide businesses with a best-in-class telematics offering while ensuring the security, privacy and integrity of our customers over the long term.”
Industry initiatives that will help increase cybersecurity
While we have gone to great lengths to help secure the connection between the vehicle and the user interface, our commitment hasn’t ended at our own walls or for our own clients. We see this as a threat to the transportation ecosystem as a whole and, because of that, we’re collaborating with industry stakeholders including SAE, IEEE, Auto-ISAC, OEMs, universities, and government regulators to share best practices developed with our customers and competitors to advance connected vehicle security.
Geotab also collaborates with the United States Department of Transportation, the Department of Homeland Security, the GENIVI Alliance and others on an ongoing basis to develop and refine cybersecurity standards for telematics.
Conclusion
As with any fleet initiative, cybersecurity isn’t a one-and-done task but an ongoing process that must be vigilantly monitored.
With our commitment to fleet data security, including adhering to FIPS protocols, support for multi-factor authentication, and permissions-based access backed by FedRAMP certification, Geotab has developed a cybersecurity profile that is strong, mature, and ever-evolving.
Having a unified approach to cybersecurity throughout the organisation, including protecting data that can be accessed from the vehicle, will protect your entire business. Leaving any part of your organisation vulnerable is an open invitation to cybercriminals and terrorists looking to steal your data, cause harm, and hurt your bottom line. With Geotab, you can effectively triple lock your vehicle’s data and keep it protected.
Learn more about Geotab’s rigorous approach to data security.

Corinda Ouellet is a Marketing Manager, Segment at Geotab.
Related posts
.jpeg)

Geotab becomes a certified Telematics Monitoring Application Service Provider
April 1, 2025
3 minute read


Geotab at MEGATRANS discusses Cost Savings and Automation
September 24, 2024
1 minute read