Federal fleet manager cybersecurity considerations for telematics
Guidance for federal fleet managers on choosing a telematics solution that is more likely to meet their agency’s minimum cybersecurity requirements.

By Neil Garrett
Oct 5, 2017
Updated: Aug 26, 2024

It can be challenging for federal fleet managers to determine what cybersecurity requirements should apply to their telematics deployments. The purpose of this document is to help guide and inform federal fleet managers, chief security officers, and other members of the fleet industry on cybersecurity standards so that they can make the right decision when choosing a telematics solution.
To better understand the technical terms included in this article, please refer to the FAQ section at the end.
1. Technical and Organizational Data Security Plan
Telematics companies should have an IT Security Plan based on NIST 800-53 that provides an overview of the technical and organizational data security measures they have implemented. The document should undergo frequent changes and updates as security measures are changed and incorporated. Subjects that should be covered in the document in order to meet federal requirements include:
- Employee Policies
- Data Centers & Technology Service Providers
- Data Transmission
- Device Security
- System Access
- Systems Monitoring
- Penetration Testing/Vulnerability Scans
- Disaster Recovery Plan
- Audits
- Process of Updating Plans
In some cases, a Risk Management Framework based on NIST 800-37 can be referenced for more stringent requirements.
2. Secure Management and Encryption of Data
Telematics companies should secure all Data in Transit (DIT) and Data at Rest (DAR). Implementing data encryption provides data privacy regardless of the state of the cellular network or any other intermediate connection medium. Implementing authentication will verify that the received/transmitted data sources and destinations are what you think they are.
Minimum Encryption and Cryptographic Modules required by the Federal Government:
- Securely encrypted end-to-end data transmission between the device and the target server, using an industry standard AES-256 DIT (Data in Transmission) encryption algorithm.
- Cryptographic modules that have been validated under FIPS 140-2.
- AES 256 DAR (Data at Rest) — All privacy and security critical data stored on the device should be encrypted using AES 256.
3. Cryptographic Module with FIPS 140-2 Compliance
A cryptographic module, found in computers and telecommunication systems, is a combination of hardware, software or firmware that performs cryptographic functions (encryption, decryption, digital signatures, authentication techniques and random number generation, etc.).
The Federal Information Processing Standard (140-2) refers to FIPS 140-2, Security Requirements for Cryptographic Modules, which is a security standard for federal organizations related to the design and implementation of cryptographic modules. The standard was issued by the National Institute of Standards and Technology. For U.S. government procurement, solutions using cryptography should complete FIPS 140-2 validation. Cryptographic module validation testing is performed only by Cryptographic and Security
Testing (CST) Laboratories, so it gives end users the peace of mind that the solution they are buying has undergone testing by an accredited lab.
4. Cloud Solutions in Non-Government Data Centers
If the IT solution and database are hosted and maintained at a non-government facility, then government managed server provider (MSP) requirements like the Federal Risk and Authorization Management Program (FedRAMP) will apply.
FedRAMP is a “government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services” which emerges from a collaboration between cybersecurity and cloud experts from different government departments and agencies (General Services Administration, National Institute of Standards and
Technology, Department of Homeland Security, Department of Defense, National Security Agency, Office of Management and Budget, and the Federal Chief Information Officer Council) and private industry. The benefits of using this approach include reducing the amount of time and staff resources needed, as well as cost savings (FedRAMP estimates 30-40% reduction of government costs).
Unless otherwise directed by the specific agency, any storage of data should be contained within the resources allocated by the contractor to support the agency. Data handling regulations may require that all data be stored and transmitted only within the contiguous United States of America. Offshore data transmission (e.g. for support services) or storage (e.g. hosted site or backup, disaster recovery) may not be permitted. For this reason, telematics service providers should use FedRAMP Infrastructure-as-a-Service CSPs such AWS GovCloud or equivalent.
5. Government Credential and Software Integration
Telematics security is not specific to the telematics device or to data storage and transmission. Telematics solutions should integrate with existing federal security procedures and user credentials. For example, government issued identification like CAC cards (DoD) and/or PIV Cards (civilian agencies) are used for accessing buildings and work terminals, and therefore the same should be used for accessing telematics services. These government issued credentials should be used to automatically sign users directly into their fleet management portal, and control their clearances accordingly (single-signon). In addition, these government IDs should be used for accurate driver identification, which allows fleet managers to properly manage driving behavior and vehicle utilization.
In some cases, telematics data needs to be incorporated into a government’s FMIS. DPAS integration (for some DoD component agencies) or Global Combat Support System (for the Army) are examples. Telematics should be securely integrated into these systems in order to automate regulatory reporting in systems such as FAST and to support other internal processes such as VAM and Fleet Management Plans.
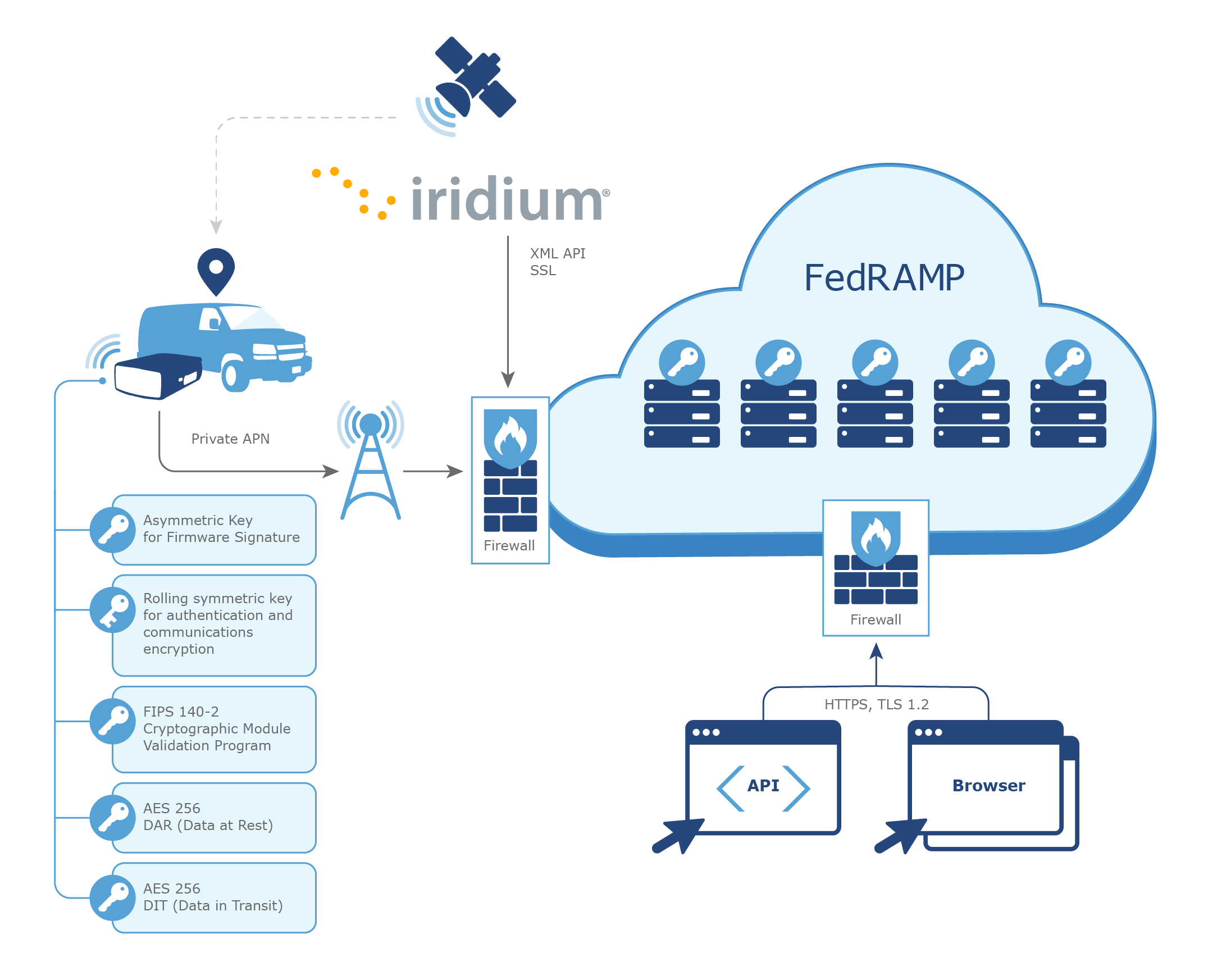
System Architecture for Telematics
Frequently Asked Questions
What is NIST?
NIST is the U.S. National Institute of Standards and Technology which produced FIPS 140-2 and other standards. NIST is one of the nation's oldest physical science laboratories.
What is FIPS 140-2?
The Federal Information Processing Standard (FIPS) 140-2 issued by NIST outlines the security requirements for cryptographic modules.
What is cryptography?
Cryptography is the practice of coding and decoding of data or information so that it remains confidential and unaltered during storage or transfer.
What are cryptographic modules?
A cryptographic module, found in computers and telecommunication systems, is a combination of hardware, software or firmware that performs cryptographic functions (encryption, decryption, digital signatures, authentication techniques and random number generation, etc.).
Why is FIPS 140-2 important?
Cryptographic modules that have been validated to FIPS 140-2 have undergone module testing by an accredited lab, the results are sent to NIST for validation, once complete the vendor is issued a certificate. Now the device can be securely used for protecting sensitive, unclassified information.
What is AES 256?
AES, or the Advanced Encryption Standard, is a symmetric-key block cipher algorithm for encrypting sensitive data. The U.S. government has adopted the use of AES to protect classified information and it is also in use around the world in hardware and software applications.
What is FedRAMP?
The Federal Risk and Authorization Management Program (FedRAMP) is a government program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services.
References:
- National Institute of Standards and Technology. (2013, Jul.). Digital Signature Standard (DSS), FIPS PUB 186-4, [Online]. Available: http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.186-4.pdf
- U.S. Department of Homeland Security, RFQ HSHQDC-17-Q-00002 Vehicle Telematics.
Related:15 Security Recommendations for Building a Telematics Platform Resilient to Cyber Threats
Subscribe to get industry tips and insights

Neil Garrett is an Associate Vice President of Business Development, Government for Geotab.
Table of Contents
Subscribe to get industry tips and insights
Related posts

9 strategies to increase fleet fuel efficiency and lower fuel costs
July 8, 2025
4 minute read

Creating a fleet safety culture that’s built to last: Lessons from Missouri DOT and NYC
July 7, 2025
8 minute read

Field service is losing money to bad data: Go beyond GPS with smarter telematics
June 27, 2025
3 minute read
